
This article is a WTF explainer, in which we break down media and marketing’s most confusing terms. More from the series →
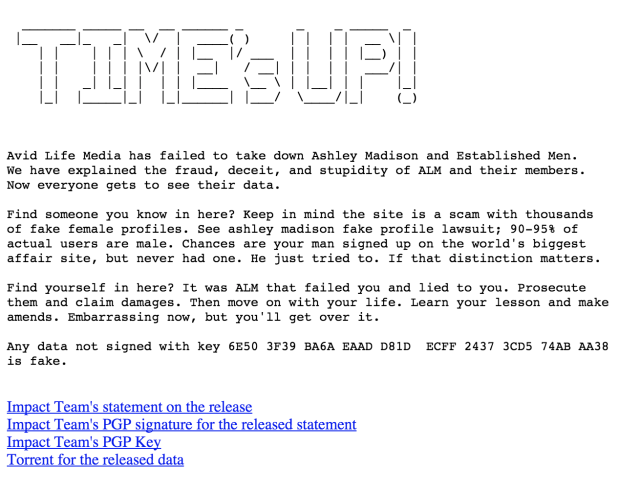
Time’s up.
That what’s hackers said late Tuesday when it released a trove of data from extramarital hookup website Ashley Madison for the world to see. The hackers weren’t kidding around when they said they would dump 10GB worth of private user data onto the Internet.
When did this all start?
Last month. The hackers, known as the Impact Team, took umbrage with the sleazy site’s mission to encourage married people to cheat on their significant others. They hacked into Avid Life Media’s servers, which owns dating websites Ashley Madison, Established Men and Cougar Life. Data from the first two websites were released, but information from the third website appeared not to be dumped.
What exactly is in the data?
A lot. Hackers released the information of 32 million people that dates back to 2007. Included in the files are credit card details, email addresses, amount paid and even internal documents about Avid Life Media’s revenue.
Perhaps one of the most shadiest pieces revealed, if that’s possible, is that Ashley Madison charged $20 to wipe their information from its servers. Apparently that was a scam. The option, called “Full Delete,” generated an additional $1.7 million last year, a “complete lie,” the hackers wrote. “Users almost always pay with credit card; their purchase details are not removed as promised, and include real name and address, which is of course the most important information the users want removed,” they said.
Avid Life Media denies the hacker’s accusation that it the feature didn’t work.
I have a, um, friend who used the service. Should my friend be worried?
Not yet, but soon. The data is only readable on Tor, a browser that only works on the dark web where traffic data is anonymous. Internet sleuths have begun combing through the data to decode it and have been posting it on Pastebin. So far, several thousand emails have a United States government domain (i.e. .mil or .gov), according to Vocativ.
There’s a big caveat about all of this. The dumped data appears to be legit, but Ashley Madison didn’t verify user’s emails, meaning someone could have registered an email but that doesn’t mean they were a user of the website.
“Journalists and commentators would be wise to remember that the credentials stored by Ashley Madison must be considered suspect because of their shonky practices, even before you start considering whether any leaked databases are falsified or not,” notes security blogger Graham Chuley.
What does Avid Life Media have to say about this?
The company released a statement this morning saying it’s working with security experts to “determine the origin, nature and scope of the incident.” Labeling the hack as a “criminal act,” the company apologized for “this unprovoked and criminal intrusion into our customers’ information.”
Can Ashley Madison survive this?
Probably not! Brand experts tell PR Week that this hack “has completely broken the trust of its client base,” while another person called it the “Wikileaks of the cheating world.” ALM’s weak security will likely scare off any other potential users who were looking to sign-up, so cheaters will have to revert back to cheating the old-fashioned way.
Image via Shutterstock.
More in Marketing

YouTube’s upmarket TV push still runs on mid-funnel DNA
YouTube is balancing wanting to be premium TV, the short-form powerhouse and a creator economy engine all at once.

Digiday ranks the best and worst Super Bowl 2026 ads
Now that the dust has settled, it’s time to reflect on the best and worst commercials from Super Bowl 2026.

In the age of AI content, The Super Bowl felt old-fashioned
The Super Bowl is one of the last places where brands are reminded that cultural likeness is easy but shared experience is earned.





